MPC-TSS Protocol Overview
Supported Signature Algorithms
The SMN suite supports the following signature algorithms under the MPC-TSS protocol:
| Primitive | Implemented Protocol | Supported Curves | Supported Threshold |
|---|---|---|---|
| ECDSA | CMP | Secp256k1 | 2/2, 2/3, 3/3, 3/5 |
| EdDSA | Lin22 | Ed25519 | 2/2, 2/3, 3/3, 3/5 |
| Schnorr | Lin22 | Secp256k1 | 2/2, 2/3, 3/3, 3/5 |
Upcoming versions will include the support of ECDSA signature algorithms for the Secp256r1 and STARK curves, while also offering enhanced flexibility in signing threshold settings.
Supported blockchains for different signature algorithms:
| Primitive | Curves | Supported Blockchains |
|---|---|---|
| ECDSA | Secp256k1 | EVM, Bitcoin, TRON, Filecoin, Dash, Bitcoin Cash, Dogecoin, Polkadot, and others |
| EdDSA | Ed25519 | NEAR, Sui, Aptos, Solana, Ripple, Stellar, and others |
| Schnorr | Secp256k1 | Bitcoin, Bitcoin Cash, Bitcoin SV, Dogecoin, and others |
Supported MPC-TSS Sub-Protocols
SMN suite supports the following MPC sub-protocols to meet various business scenarios. Let's take the 2/2 threshold scenario as example.
Distributed Key Generation

This protocol is applicable to wallet creation scenarios. Each party generates their own local key share through the Distributed Key Generation (DKG) protocol, and throughout the process, the original private key never appears. Each party's input to the DKG protocol can be regarded as a locally generated random number, and the output is the key share. Each party can only obtain its own key share, which can be used for distributed signing protocols, etc.
Distributed Key Signing
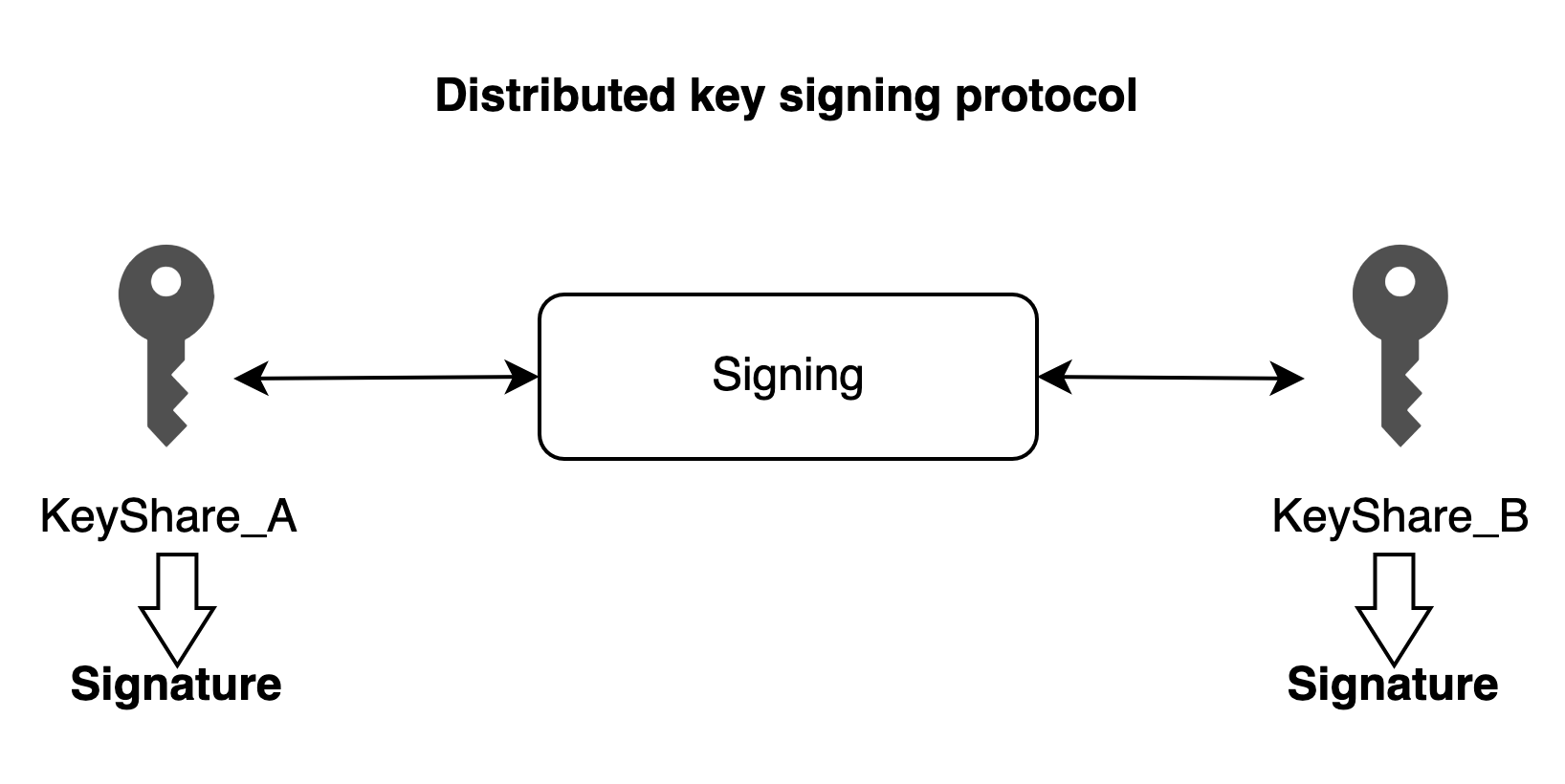
This protocol is suitable for transaction signing scenarios. Each party generates a same signature for the message by running the Distributed Key Signing protocol. Each party can obtain the signature result, and the original private key does not appear throughout the process. Each party's input to the Distributed Key Signing protocol includes its local key share and the message to be signed, and the output is the signature for the message.
Derived Distributed Key Signing
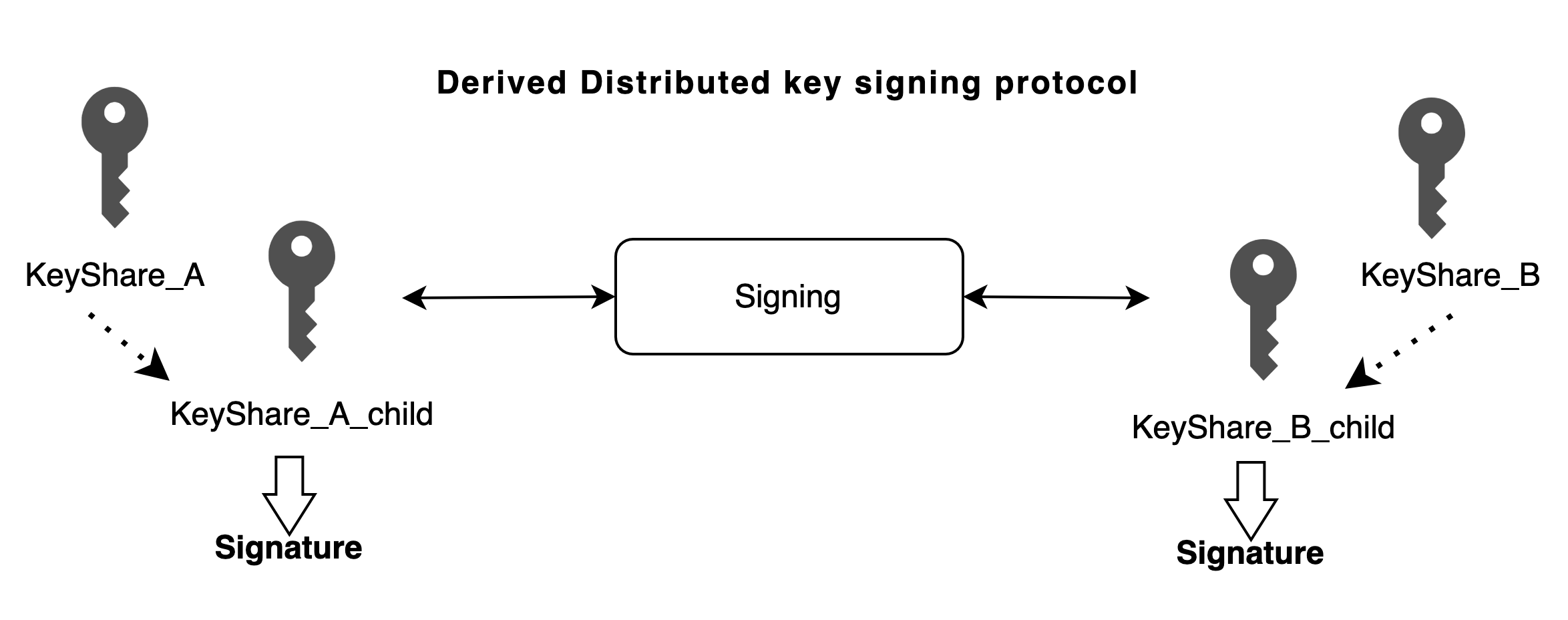
This protocol is applicable to HD wallet transaction signing scenarios. In a single-key signing system, sub keys can be derived from a seed key according to a specified path, and these sub keys can be used for signing. The advantage is that only the seed key needs to be backed up and managed, and an infinite number of sub keys can be managed through the derivation mechanism. An MPC protocol can also implement similar derivation logic. After adding the derivation function to the Distributed Key Signing protocol, a group of key shares can manage an infinite number of sub-key shares. Therefore, the input to the Distributed Key Signing protocol are the local key share, the path for deriving the sub-key share, and the message to be signed. The output remains the same, which is the signature for the message.
Distributed Key Refreshing
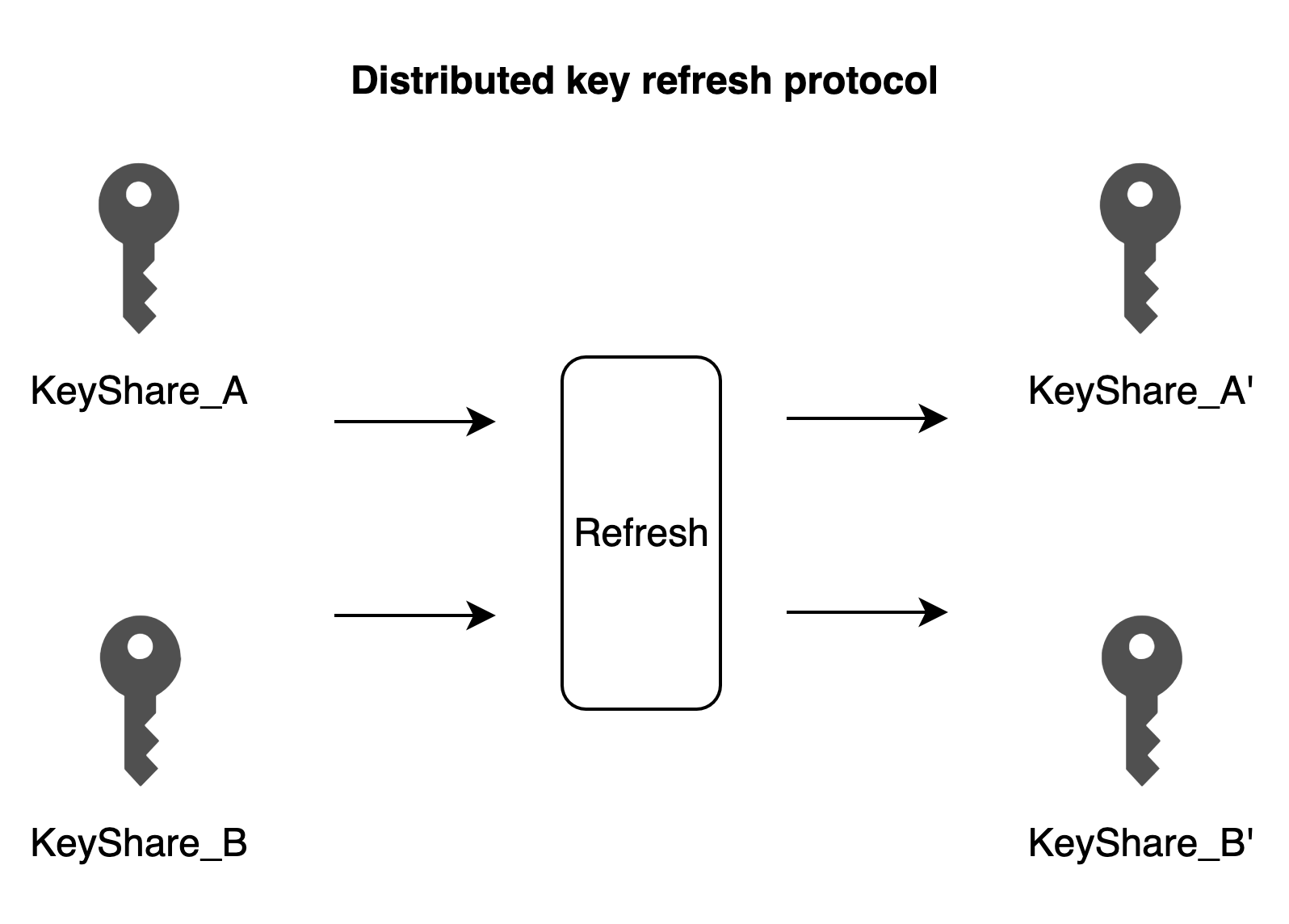
This protocol is applicable to secure refreshing of wallet key shares. The old set of key shares can be refreshed to obtain a new set of key shares through the Private Key Refreshing protocol. The input to the protocol is each party's key share, and the output is the new key share. It is important to note that the old key shares remain usable, and developers need to decide whether to disable the old ones based on your business scenarios.
Distributed Key Recovery
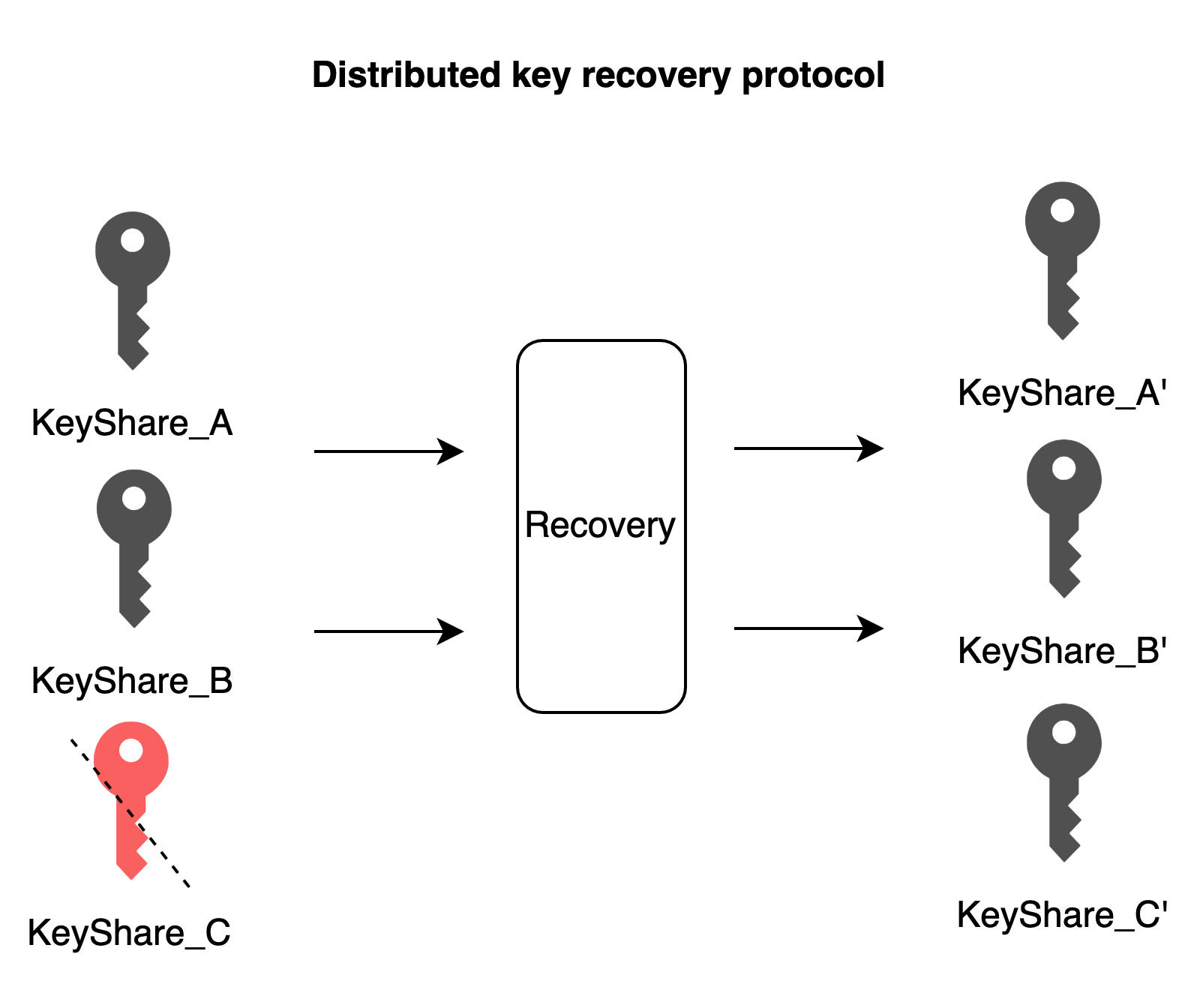
This protocol is applicable to 2/3 threshold MPC wallets, where one party's key share is lost/discarded, and the scenario requires recovery of the key share. In a 2/3 threshold scenario with 3 key shares, if one key share is lost, it can be recovered using the Distributed Key Recovery protocol. The input is the existing two key shares, and the output is a new set of three key shares. It is important to note that the old key shares A and B remain usable, and developers need to decide whether to disable them based on your business scenarios.
Summary
SMN suite helps developers quickly build upper-layer applications by providing underlying MPC-TSS protocols, eliminating the need for concern with cryptographic details. Developers can use different MPC protocols to build business systems according to your business scenarios.